Kali Linux (successor of BackTrack Linux) is a free and open-source Debian-based Linux distribution funded and maintained by Offensive Security from Switzerland. Users can boot and use this OS via hard disk, live CD or live USB anytime and anywhere. Almost all open-source tools used for digital forensics, penetration testing, ethical hacking and network security assessments are included. There is no need to prepare and maintain this Linux distribution (including gathering all those software and their dependencies) by yourself, or to install any software and save any files on Kali.
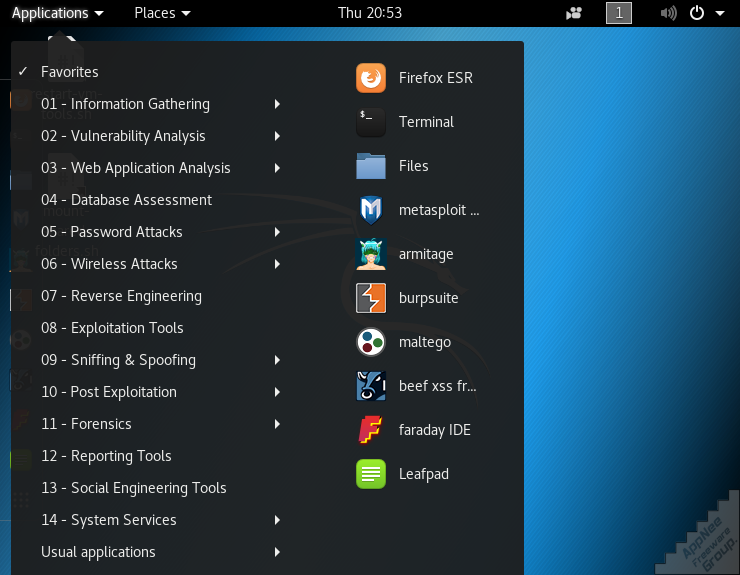
Kali Linux is done by rewriting the famous and popular BackTrack, and preloaded with hundreds of penetration testing software: classic information acquisition tools suck like Nmap and Wireshark; WiFi-oriented tools like Aircrack-ng, Kismet and Pixie; tools for cracking passwords like THC-Hydra, crunch, hashcat and John the Ripper; and more suites of toolkits, including Metasploit and Burp Suite. To sum up, “a hacker’s toolkit” is not enough to describe it. Instead, it can be regarded as “a huge hacker’s operating system” that covers multiple security areas, such as wireless networks, digital forensics, servers, passwords, system vulnerabilities, and more.
Because it’s specially built for professional penetration testings and security audits (which may be all you need to use it for), Kali Linux has made a number of core changes. For example: It’s designed to log in with single-root authority; Disables the network services by default (but allows users to install them manually); Allows users to install various packages; Comes with customized kernels, etc. Therefore, you cannot use it as an normal operating system for daily use. Instead, it is an aggressive system that lacks security assurance (rather than a safety-focused defensive system). You can see that it is not secure just because it is designed to run under the root authority only.
Key Features
- Full Customisation of Kali ISOs
- Kali Linux ISO of Doom and Other Kali Recipes
- Kali Linux Live USB with LUKS Encrypted Persistence
- Kali Linux Live USB with Multiple Persistence Stores
- Kali Linux Full Disk Encryption
- Kali Linux LUKS Encryption Nuke
- Kali Linux Metapackages
- Kali Linux Amazon EC2 AWS Images
- Kali Linux Accessibility Features
- Automating Kali Linux Deployment
- Kali Linux on a Raspberry Pi and Other ARM Devices
- Kali Linux Forensics Mode
- Kali Linux NetHunter
- Kali Linux Running on Android
- Disk Encryption on Raspberry Pi 2
Official Demo Video
Prompts
- The default password for the username root is: toor
Download URLs
| License | Version | Images | Virtual Images |
| Free OS | Latest |  (mir) (mir) |  |



No comments:
Post a Comment